Oct 7, 2022
Hackers Feast on Crypto Weak Link and Even Binance Isn’t Spared
, Bloomberg News
(Bloomberg) -- There’s a gaping hole in the crypto industry’s security architecture, and even the most deep-pocked players haven’t figured out how to plug it.
The weakness in question is what’s known in industry parlance as cross-chain bridges -- software that allows crypto tokens to move between different blockchains.
On Thursday, a hacker made off with about $100 million via a bridge used by Binance Holdings Ltd., crypto’s largest exchange.
“The worrying thing about this is that Binance are not fools, Binance have got capital, resources and are able to hire the best,” said Paddy Cerri, chief architect at blockchain startup Minima. “If they can’t do this, who exactly can build a secure bridge?”
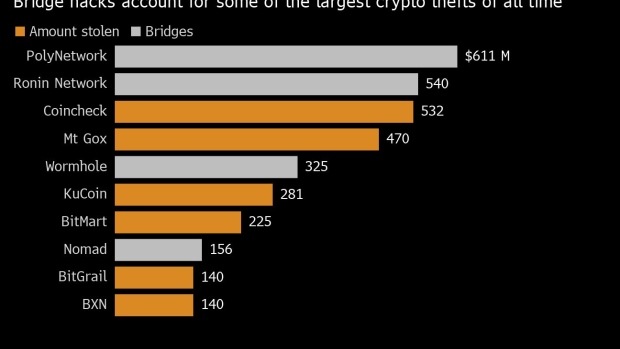
A total of 2 million Binance Coin -- equivalent to nearly $570 million -- were effectively minted and taken by the hacker. Binance said in a statement that the incident was isolated to BNB Chain, over which it doesn’t exert control. About $100 million of the stolen funds were not recovered, while the rest were frozen, according to the statement. No user funds were lost, Binance added.
The inability to make bridges safe -- Chainalysis estimates that $2 billion worth of tokens have been looted from 13 separate attacks, the majority of which was stolen this year -- presents a fundamental dilemma, because without such platforms, major blockchains from Ethereum to Solana remain largely segregated from each other. The vision behind web3, billed by protagonists as the internet’s next iteration, rests in part on tokens flowing freely between various ecosystems.
Underscoring the demand for this technology, protocols built around cross-chain bridges and interoperability have raised around $347 million across 30 deals since 2021, according to Kunal Goel, a research analyst at Messari. LayerZero had the largest deal where it raised $135 million but most of the deals have been seed rounds, Goel said.
Watch: About $100 Million in Binance Coin Stolen
But even well-funded bridges built specifically to be “security-first” have not been spared. In August, one such bridge called Nomad -- which uses a method for verifying transactions that it says is safer than those used by other cross-chain platforms -- was hit by a $200 million hack.
One of the major challenges around building secure bridges is their complexity, which gives hackers many potential entry points. And there are few qualified experts who can build and secure them, security analysts and blockchain developers say. Bridge developers must not only be deeply knowledgeable about how the software works, but also about the functioning of the different blockchains it connects to. Finding someone with this knowhow is not easy, according to analysts and programmers.
“I have studied distributed computing and consensus and yet I must say don’t understand bridges well,” said Paul Frambot, chief executive officer of crypto startup Morpho Labs, which developed a new protocol. “This is very hard to understand well and so even harder to build secure ones.”
Bridges are open-source software, so their code is available for everyone to see. This is a double-edged sword: It makes them more naturally vulnerable to hacks than traditional financial networks, such as the private ones operated by banks, but also allows more individuals to help improve the code, experts said.
“In the short term the code being open-source allows malicious actors to spot vulnerabilities in libraries and packages that have been recently built and developed,” said David Kroger, a digital data scientist at Cowen Digital. “However, being open-source allows communities to come together exposing attack surfaces early to be taken care of before it becomes detrimental.”
Another issue with bridges is that most operate with a small set of custodians or entities such as validators that are responsible for securing the network. This makes them vulnerable as they sacrifice decentralization for the sake of operating at scale.
Pesky Bugs
Bugs are also common on bridges, in part because the technology being used is very new, security experts said. But there is a silver lining.
“Secure bridge design is still a technical challenge that the industry is trying to resolve through trial and error,” said Adrian Hetman, tech lead of triaging at bug bounty hunter site Immunefi. “With every new hack and security bug found, we can learn from the mistakes and build better solutions.”
Developers still don’t have many tools for creating, debugging or supporting bridge software, though, nor basic operating standards, Chase Devens, a research analyst at Messari, wrote in a July report.
On top of technical challenges, developers building bridges are facing more dangerous enemies. Lazarus, a North Korea state-backed hacking group, was identified as the attacker behind Ronin Bridge hack and $100 million Horizon Bridge theft in June. To fend off savvy hackers with vast resources and prove they can be more than a costly headache for the sector, bridges may face no choice but to step up their game, security experts said.
“We are still in the infancy stage,” says Mudit Gupta, chief information security officer at Ethereum scaling solution Polygon. “There’s a lot more work that needs to happen.”
©2022 Bloomberg L.P.





